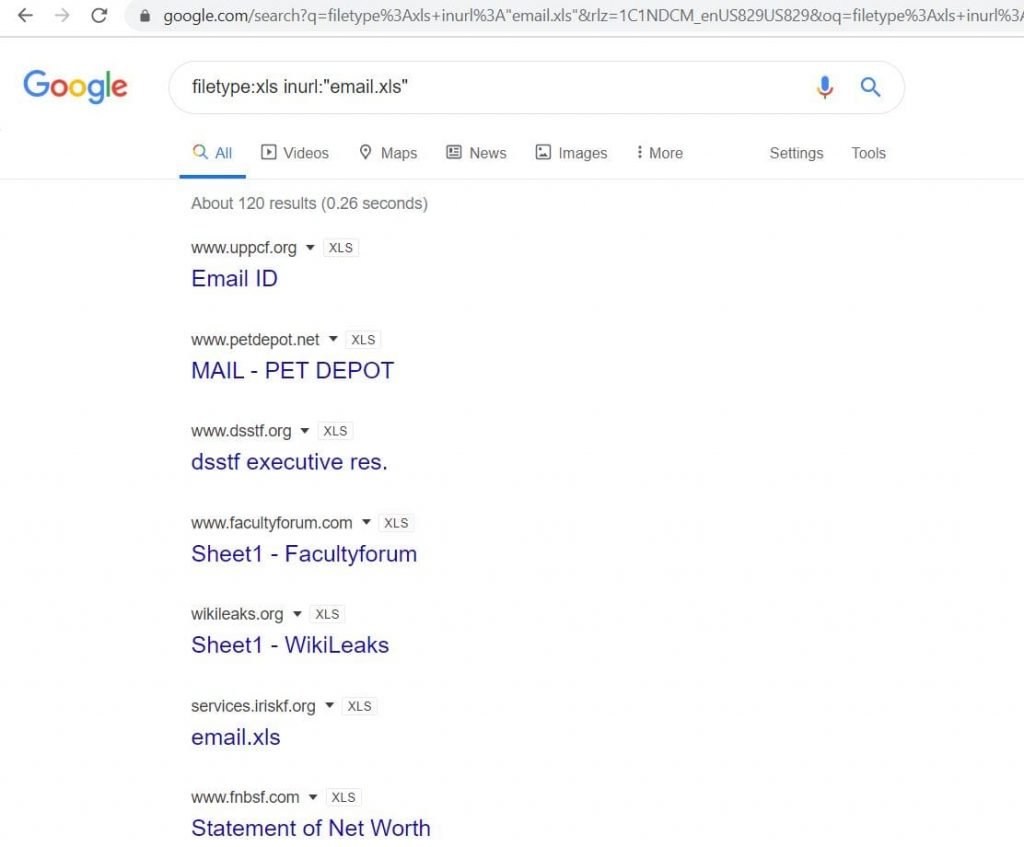
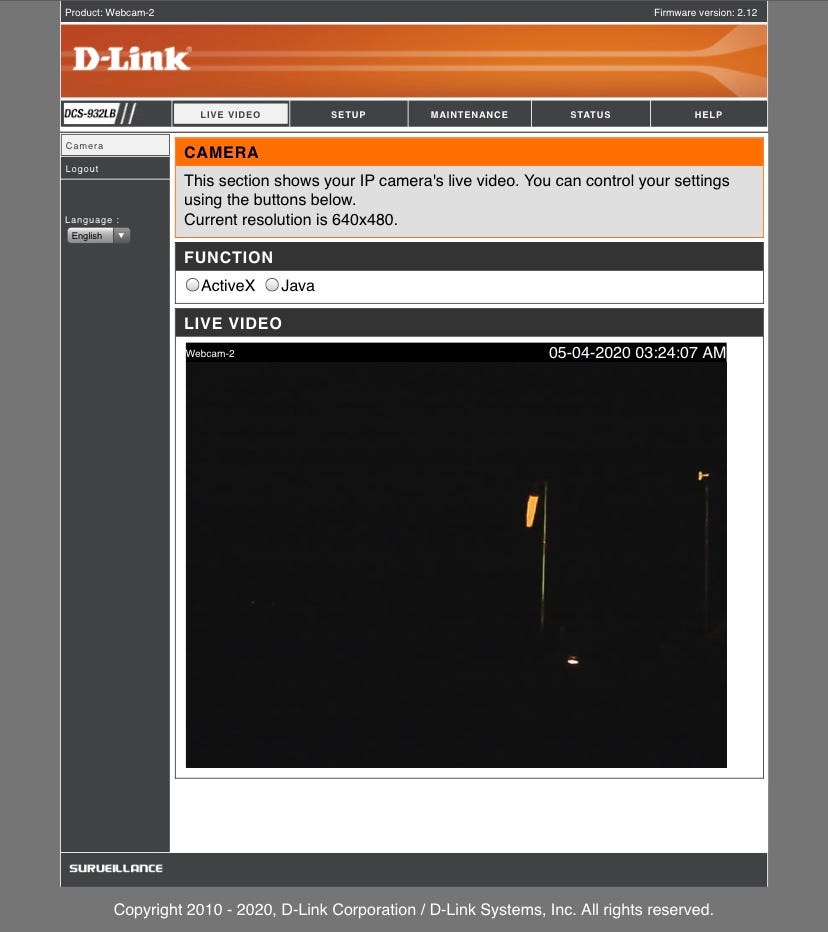
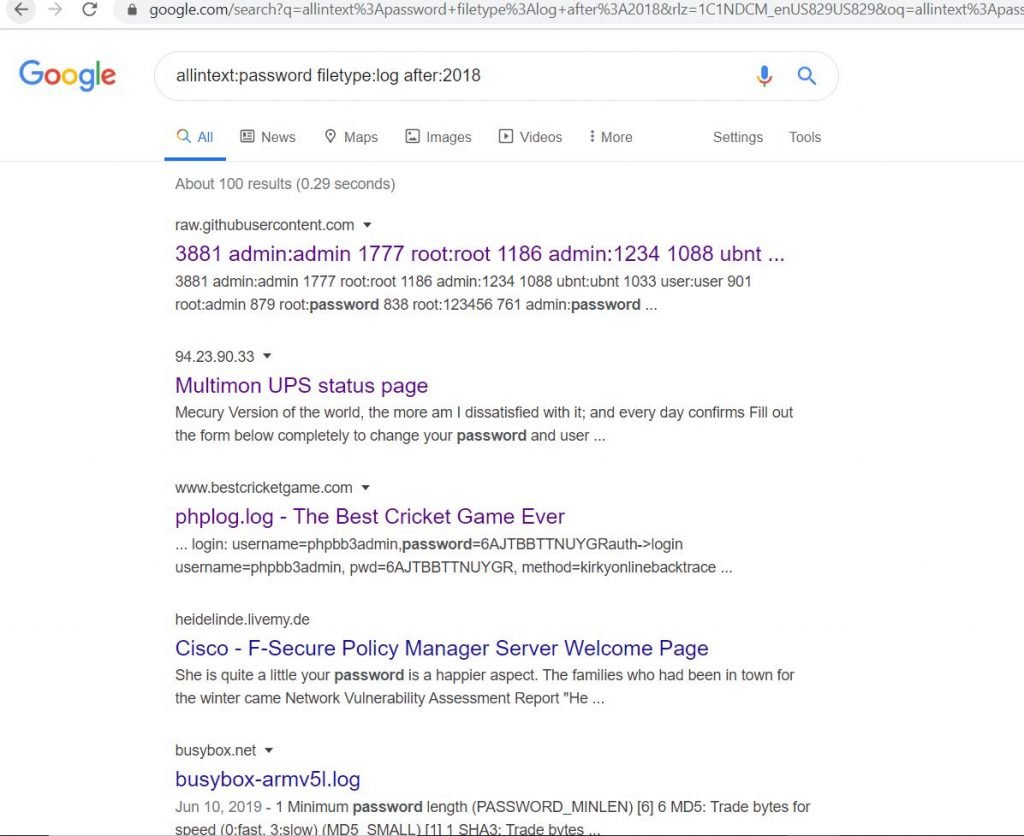
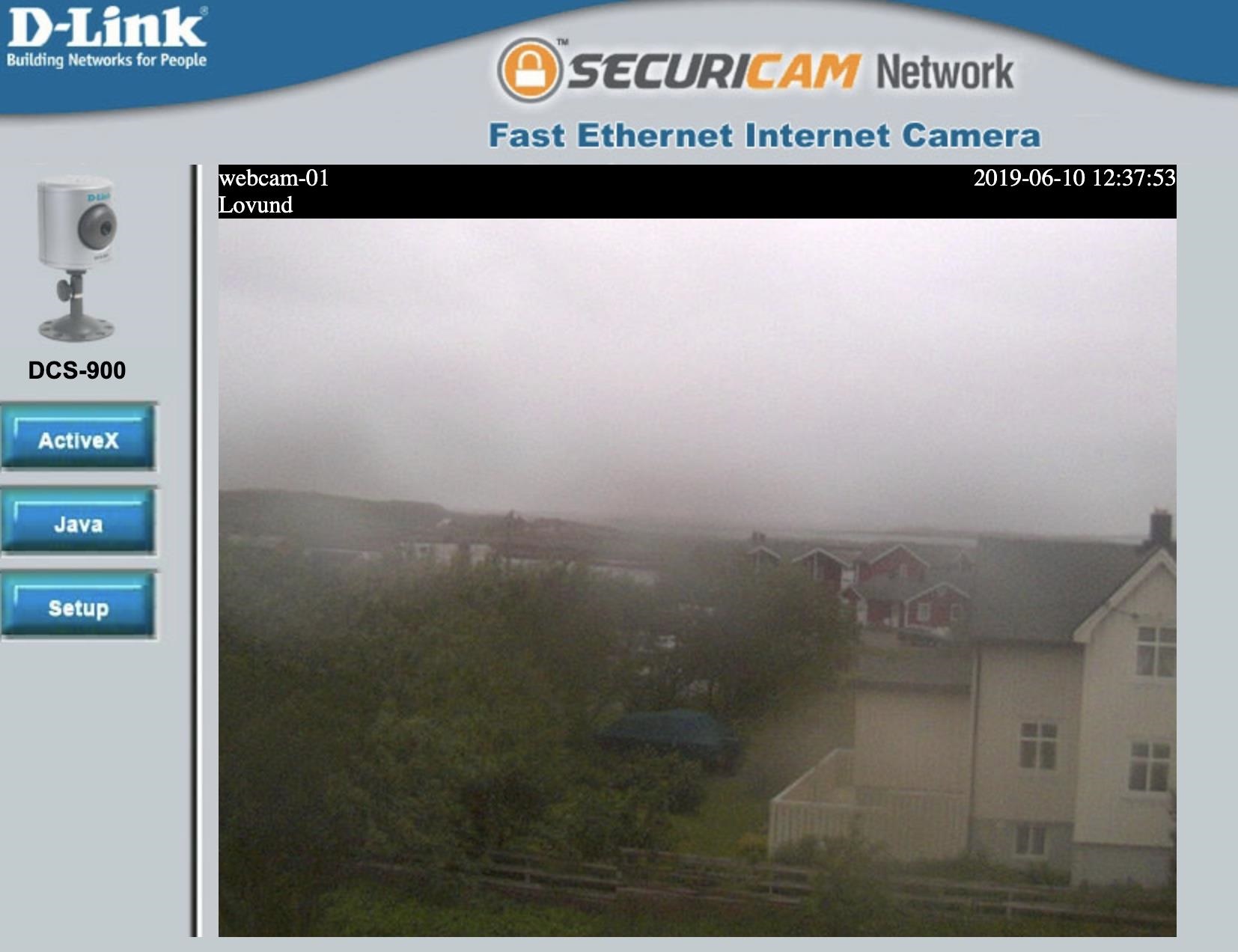
A Hacker's Guide to Google Dorks. Want to get more out of your Google… | by CoolTechZone - Cyber Security Labs & News | Medium

Google Dork: hacking di siti web grazie alla ricerca su Google | Marino Luigi: Senior iOS Developer, IT Project Manager e CTO

Firm specialization in clean energy technologies: The influence of path dependence and technological diversification | Cairn International Edition